Microsoft Antimalware for Azure Cloud Services and Virtual Machines
- ALIF Consulting

- Nov 4, 2022
- 4 min read
Updated: Jun 11, 2024
Microsoft Antimalware for Azure is a free real-time protection that helps identify and remove viruses, spyware, and other malicious software. It generates alerts when known malicious or unwanted software tries to install itself or run on your Azure systems.
The solution is built on the same antimalware platform as Microsoft Security Essentials [MSE], Microsoft Forefront Endpoint Protection, Microsoft System Center Endpoint Protection, Microsoft Intune, and Microsoft Defender for Cloud. Microsoft Antimalware for Azure is a single-agent solution for applications and tenant environments designed to run in the background without human intervention. Protection may be deployed based on the needs of application workloads, with either basic secure-by-default or advanced custom configuration, including antimalware monitoring.
When you deploy and enable Microsoft Antimalware for Azure for your applications, the following core features are available:
Core Features
Real-time protection
Monitors activity in Cloud Services and on Virtual Machines to detect and block malware execution.
Scheduled scanning
Scans periodically to detect malware, including actively running programs.
Malware remediation
Automatically takes action on detected malware, such as deleting or quarantining malicious files and cleaning up malicious registry entries.
Signature updates
Automatically installs the latest protection signatures (virus definitions) to ensure protection is up-to-date on a pre-determined frequency.
Antimalware Engine updates
Automatically updates the Microsoft Antimalware engine.
Antimalware Platform updates
Automatically updates the Microsoft Antimalware platform.
Active protection
Reports telemetry metadata about detected threats and suspicious resources to Microsoft Azure to ensure rapid response to the evolving threat landscape, as well as enabling real-time synchronous signature delivery through the Microsoft Active Protection System (MAPS).
Samples reporting
Provides and reports samples to the Microsoft Antimalware service to help refine the service and enable troubleshooting.
Exclusions
Allows application and service administrators to configure exclusions for files, processes, and drives.
Antimalware event collection
Records the antimalware service health, suspicious activities, and remediation actions taken in the operating system event log and collects them into the customer's Azure Storage account.
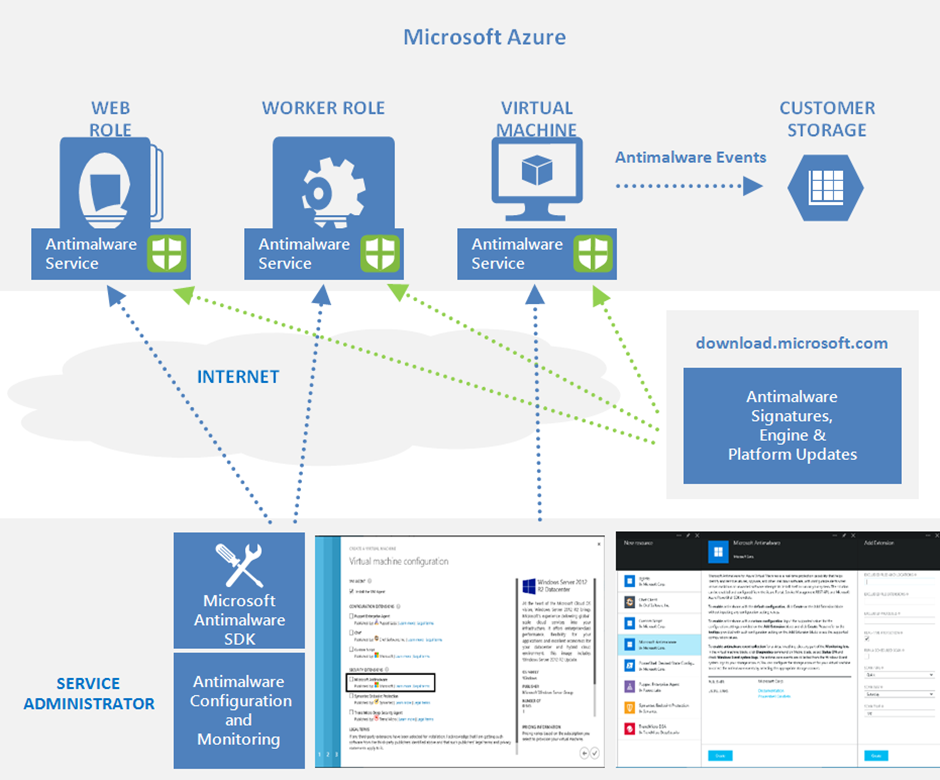
Architecture
Microsoft Antimalware for Azure includes the Microsoft Antimalware Client and Service, Antimalware classic deployment model, Antimalware PowerShell cmdlets, and Azure Diagnostics Extension. Microsoft Antimalware is supported on Windows Server 2008 R2, Windows Server 2012, and Windows Server 2012 R2 operating system families. It is not supported on the Windows Server 2008 operating system, and also is not supported in Linux.
The Microsoft Antimalware Client and Service is installed by default in a disabled state in all supported Azure guest operating system families in the Cloud Services platform. The Microsoft Antimalware Client and Service is not installed by default in the Virtual Machines platform and is available as an optional feature through the Azure portal and Visual Studio Virtual Machine configuration under Security Extensions.
When using Azure App Service on Windows, the underlying service that hosts the web app has Microsoft Antimalware enabled on it. This is used to protect Azure App Service infrastructure and does not run on customer content.
Microsoft Antimalware Workflow
The Azure service administrator can enable Antimalware for Azure with a default or custom configuration for your Virtual Machines and Cloud Services using the following options:
Virtual Machines – In the Azure portal, under Security Extensions
Virtual Machines – Using the Visual Studio virtual machines configuration in Server Explorer
Virtual Machines and Cloud Services – Using the Antimalware classic deployment model
Virtual Machines and Cloud Services – Using Antimalware PowerShell cmdlets
The Azure portal or PowerShell cmdlets push the Antimalware extension package file to the Azure system at a pre-determined fixed location. The Azure Guest Agent (or the Fabric Agent) launches the Antimalware Extension, applying the Antimalware configuration settings supplied as input. This step enables the Antimalware service with either default or custom configuration settings. If no custom configuration is provided, then the antimalware service is enabled with the default configuration settings
Once running, the Microsoft Antimalware client downloads the latest protection engine and signature definitions from the Internet and loads them on the Azure system. The Microsoft Antimalware service writes service-related events to the system OS events log under the "Microsoft Antimalware" event source. Events include the Antimalware client health state, protection and remediation status, new and old configuration settings, engine updates and signature definitions, and others.
You can enable Antimalware monitoring for your Cloud Service or Virtual Machine to have the Antimalware event log events written as they are produced to your Azure storage account. The Antimalware Service uses the Azure Diagnostics extension to collect Antimalware events from the Azure system into tables in the customer's Azure Storage account.
The deployment workflow, including configuration steps and options supported for the above scenarios, is documented in the Antimalware deployment scenarios section of this document.
Default and Custom Antimalware Configuration
The default configuration settings are applied to enable Antimalware for Azure Cloud Services or Virtual Machines when you do not provide custom configuration settings. The default configuration settings have been pre-optimized for running in the Azure environment. Optionally, you can customize these default configuration settings as required for your Azure application or service deployment and apply them to other deployment scenarios.
The following table summarizes the configuration settings available for the Antimalware service. The default configuration settings are marked under the column labelled "Default" below.

Antimalware Deployment Scenarios
The scenarios to enable and configure antimalware, including monitoring for Azure Cloud Services and Virtual Machines, are discussed in this section.
Deployment While creating a VM using the Azure portal
Deployment using the Visual Studio virtual machine configuration
Deployment Using PowerShell cmdlets
Enable and Configure Antimalware Using PowerShell cmdlets



